Featured
Table of Contents
What An Ipsec Vpn Is, And How It Works
These settlements take 2 types, primary and aggressive. The host system that begins the process suggests encryption and authentication algorithms and settlements continue till both systems choose the accepted protocols. The host system that starts the process proposes its favored file encryption and authentication techniques however does not work out or change its choices.
Once the data has been moved or the session times out, the IPsec connection is closed. The personal secrets used for the transfer are deleted, and the procedure pertains to an end. As demonstrated above, IPsec is a collection of various functions and actions, comparable to the OSI model and other networking structures.
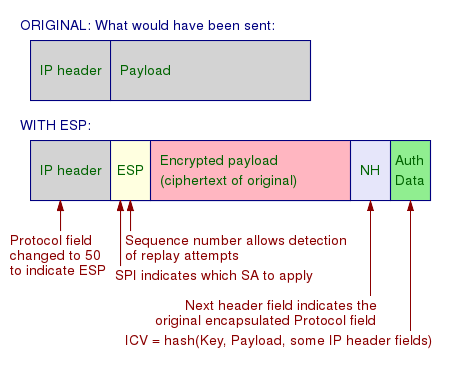
IPsec utilizes two primary protocols to supply security services, the Authentication Header (AH) procedure and the Encapsulating Security Payload (ESP) procedure, together with a number of others. Not all of these procedures and algorithms need to be used the particular selection is identified throughout the Negotiations stage. The Authentication Header protocol confirms information origin and stability and supplies replay protection.
Ipsec - Wikipedia
A trusted certificate authority (CA) offers digital certificates to authenticate the communication. This permits the host system receiving the information to validate that the sender is who they claim to be. The Kerberos procedure supplies a centralized authentication service, enabling devices that utilize it to confirm each other. Various IPsec executions may use different authentication methods, but the result is the exact same: the safe transfer of data.
The transport and tunnel IPsec modes have several essential differences. Transport mode is mainly utilized in scenarios where the 2 host systems interacting are relied on and have their own security procedures in place.
File encryption is used to both the payload and the IP header, and a new IP header is contributed to the encrypted package. Tunnel mode supplies a protected connection in between points, with the original IP packet covered inside a brand-new IP packet for extra defense. Tunnel mode can be used in cases where endpoints are not relied on or are doing not have security mechanisms.
Guide To Ipsec Vpns - Nist Technical Series Publications
This indicates that users on both networks can engage as if they were in the very same area. Client-to-site VPNs enable private gadgets to connect to a network from another location. With this option, a remote employee can run on the same network as the rest of their team, even if they aren't in the exact same area.
(client-to-site or client-to-client, for example) most IPsec topologies come with both advantages and drawbacks. Let's take a more detailed look at the advantages and downsides of an IPsec VPN.
An IPSec VPN is flexible and can be set up for various use cases, like site-to-site, client-to-site, and client-to-client. This makes it a great alternative for companies of all shapes and sizes.
Ipsec


IPsec and SSL VPNs have one primary difference: the endpoint of each procedure. An IPsec VPN lets a user connect remotely to a network and all its applications.
For mac, OS (via the App Shop) and i, OS versions, Nord, VPN utilizes IKEv2/IPsec. This is a combination of the IPsec and Web Key Exchange version 2 (IKEv2) protocols.
Stay safe with the world's leading VPN.
Ipsec Vpn
Before we take a dive into the tech stuff, it's essential to discover that IPsec has rather a history. It is interlinked with the origins of the Internet and is the result of efforts to establish IP-layer encryption techniques in the early 90s. As an open procedure backed by constant advancement, it has shown its qualities over the years and although challenger procedures such as Wireguard have actually occurred, IPsec keeps its position as the most widely used VPN protocol together with Open, VPN.
As soon as the interaction is established, IPSEC SA channels for secure data transfer are established in phase 2. Attributes of this one-way IPsec VPN tunnel, such as which cipher, method or key will be utilized, were pre-agreed by both hosts (in case of IPsec VPN, this is a connection between a gateway and computer).
IPsec VPNs are extensively utilized for several reasons such as: High speed, Extremely strong ciphers, High speed of developing the connection, Broad adoption by operating systems, routers and other network gadgets, Naturally,. There are alternative choices out there such as Open, VPN, Wireguard and others (see the list of essential VPN protocols on our blog site).
What Is Ipsec (Internet Protocol Security)?
When developing an IKEv2 connection, IPsec uses UDP/500 and UDP/4500 ports by default. By standard, the connection is established on UDP/500, but if it appears during the IKE facility that the source/destination lags the NAT, the port is switched to UDP/4500 (for information about a technique called port forwarding, inspect the short article VPN Port Forwarding: Great or Bad?).
There are numerous differences in terms of innovation, usage, benefits, and drawbacks. to secure HTTPS traffic. The purpose of HTTPS is to secure the material of interaction between the sender and recipient. This makes sure that anybody who wishes to obstruct interaction will not have the ability to find usernames, passwords, banking information, or other delicate information.
IPsec VPN works on a different network layer than SSL VPN. IPsec VPN operates on the network layer (L3) while SSL VPN operates on the application layer.
Internet Protocol Security Explained
When security is the main concern, modern-day cloud IPsec VPN should be picked over SSL since it encrypts all traffic from the host to the application/network/cloud. SSL VPN protects traffic from the web browser to the web server just. IPsec VPN safeguards any traffic between two points identified by IP addresses.
The issue of choosing in between IPsec VPN vs SSL VPN is carefully related to the topic "Do You Need a VPN When The Majority Of Online Traffic Is Encrypted?" which we have covered in our current blog site. Some might believe that VPNs are barely essential with the increase of built-in file encryption straight in e-mail, web browsers, applications and cloud storage.
Latest Posts
The 6 Best Vpn Stocks To Buy Right Now For August 2023
Best Vpn According To Reddit In 2023
Best Vpn Services Of 2023